WHUCTF2025 WP
WP
MISC
[签到]益智游戏
1.数独
数独还没做完,直接爆破就出了。
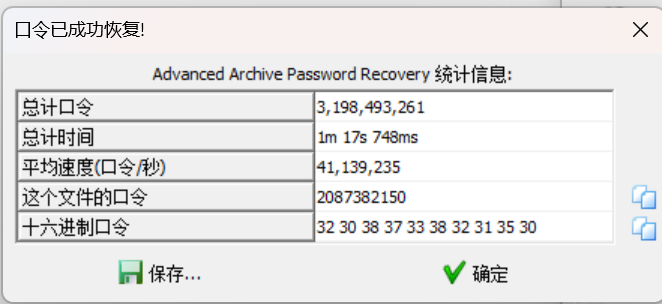
得到WHUCTF{Little_games_reall
2.数织
队友很强,直接手搓了。
得到y_train_your_brain_&_play
3.鬼脚图
直接白给了。。。
得到_more_in_cn.puzzle_website}
哪里有文档
附件是一个docx文档,而且直接给出了part1。
part2:ctrl+A一下,发现在文章最后,改一下字体颜色就看到了。
part3:ctrl+F一下,搜索part,发现一个非常隐秘的文本框,放大一下,找到part3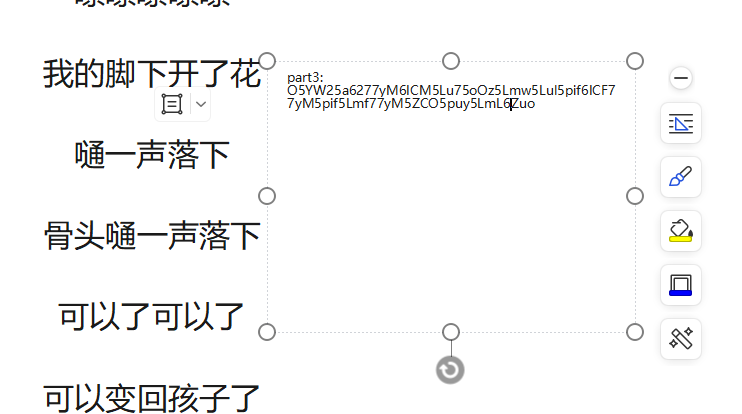
part4: 由于docx文档本质是压缩包,可以解压出一个文件夹,在docprops文件夹下边的custom文件中发现part4.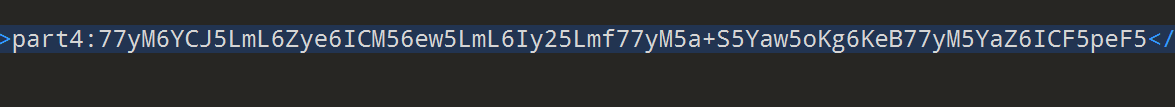
part5: 在word文件夹下边的vbaProject.bin文件中发现非疑似part5的字符串,后来试了一下还真是。
解密器: 在文档页脚的地方发现有东西,换一下字体颜色便发现,by Abracadabra encoder,上网搜索之后发现是魔曰。
解密步骤: 将5段part拼接后进行base64解码,得到一段文字,
鹏无局,无以致天,光有能听,竹有善然,虽无楼鸢之彰,亦报以畅看瀚水,求将与其家,而任想买以星者,星也,后曲之雨,选之霞而称之茶也,寒冰悠见,写者旅之,叶流而清梦看也,报在莹鹤。
放在魔曰解码器中解码得到flag
WHUCTF{always_follow_your_heart}
行星防御理事会
附件为一个wav音频,放到Audacity中查看波形图,觉得类似sstv,放入RX-SSTV工具中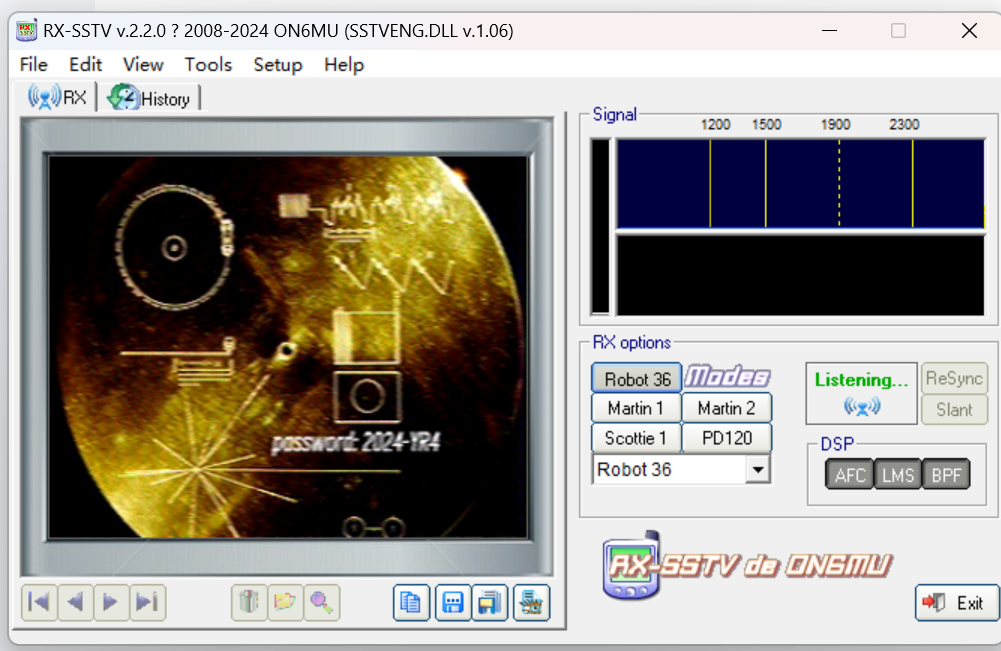
发现有密码2024-YR4,联想需要密码的wav音频隐写,在Deepsound中输入密码后得到附件,解压后是一个变形过的二维码和一个变形脚本。编写恢复脚本
1 | |

扫码得到flag。
青轴还是红轴
wireshark打开附件,发现全是USB协议流量,结合题目猜测是键盘流量。
在kali中使用tshark提取键盘流量
tshark -r raw_keyboard.pcapng -T fields -e usbhid.data > usbdata.txt
然后用脚本对提取出的流量进行处理。
1 | |
输出为output :ijniokj tfcfg fgtrdcv iuhbghj jkiuhnm ygvgh_ijnjkmn uhbn tgbnjujm ghytfvb_fghygvb ygbnju <DEL>_eszsd dfresxc hgvbhuhb_uyhbv dcfvg hbu hjkijnm uygbn eszsdx
低头看看键盘,就会发现每一组字母都是在键盘上拼出一个一个字母的形状。
最后得到prefer_blue_to_red_switch
Crypto
LFSR_Signin
题目:
1 | |
分析: 通过代码可以发现,生成时,每个最后边生成的二进制数字都是由前边的一些数字异或得到,逆向来分析,同理,每个靠前的数字也都可以由后边的一些数字得到。
由此,我们便可以从第255位开始,反向一个一个求出前255个数字。
解答:
1 | |
得到flagwhuctf{quit3_ea5y_Sign1n_R1ght?}
RSAASR
题目:
1 | |
分析: 剪枝题,直接打板子,具体可参考Crypto趣题-剪枝 | 糖醋小鸡块的blog
解答:
1 | |
Pollard & Williams
题目:
1 | |
分析: 可以看出,flag被分成了四部分,而且前两个之间存在关系,后两个之间存在关系。
重点在于p2 = (p1 - 1) // 2,p2 = (p1 + 1) // 2,我们来逐个分析。
Part1:
$$ \because p_2=(p_1-1)//2 \\ \therefore 2*N_2=2*p_2*q_2=(p_1-1)q_2 \\ 即 p_1-1|2*N2 \\ \therefore a^{2*N_2} \equiv a^{q_2*(p1-1)}\equiv1 \mod p_1 \\ \therefore a^{2*N_2}-1 = kp_1 \\ 当然 a^{2*N_2}-1 \mod N_1 = kp_1 \\ \therefore p_1=gcd(a^{2*N2}-1 \mod N_1,N_1) $$之后$q_1,p_2,q_2$便都能求出来,之后就是简单的RSA
Part2:
对于william p+1光滑算法中,p+1为光滑数,设B为p+1最大的光滑因子,要求得下标为B的阶乘B!卢卡斯序列,目的就是保证(p+1)|B!,而本题中能够看出$2*N_4=(p_3+1)*q_4$必然是$(p_3+1)$的整数倍。
之后就利用卢卡斯序列的性质来求$p_3。即p_3|(V_{2*N_4}-2)$
$\therefore p_3|gcd(V_{2*N_4}-2,N_3)$
$\therefore p_3=gcd(V_{2*N_4}-2\mod N_3,N_3)$
之后同上,脚本如下
解答:
1 | |
ez_lattice
题目:
1 | |
参考: Wiener’s v.s Lattices —— Ax≡y(mod P)的方程解法笔记 | Tover’s Blog
分析: flag又被分成了两部分,感谢出题人总是先送我一半flag。
part1: 非常常规的格,构造
$$ (a[0],a[1],k) \begin{pmatrix} 1 & 0 & X[0] \\ 0 & 1 & X[1] \\ 0 & 0 & p \\ \end{pmatrix} =(a[0],a[1],b_1+b_2) $$part2:
参考了大佬博客之后才有思路,总之就是要把X[2],X[3]分开来讨论,构造格
AM=B :
$$ (k_1k_2,a_1k_2,a_2k_1,a_1a_2) \\ \begin{pmatrix} 1 & P & 0 & P^2 \\ 0 & X_1 & X_1 & X_1P \\ 0 & 0 & -X_2 & X_2P \\ 0 & 0 & 0 & X_1X_2\\ \end{pmatrix}\\ =(k_1k_2,k_2(b_1-sk_1),b_1k_2-b_2k_1,(b_1-k_1s)(b_2-k_2s) $$由于这个格并不满足Hermite定理,因此需要配平,配平系数可以参考大佬博客。
$$ B \approx (P^{2\alpha},P^{2\alpha+\gamma},P^{\alpha+\beta},P^{2\alpha+2\gamma})\\ \begin{pmatrix} P^{2\gamma} & 0 & 0 & 0\\ 0 & P^{\gamma} & 0 & 0 \\ 0 & 0 & P^{\alpha-\beta+2\gamma} & 0 \\ 0 & 0 & 0 & 1\\ \end{pmatrix} $$其中$\gamma=\frac12,\alpha=\frac{5}{14},\beta=0$
求出矩阵B之后再乘上M的逆,从而得到矩阵A,再利用a中关系求出$a_1,a_2$
解答:
1 | |
Siesta’s_revenge
题目:
1 | |
分析: 怎么说呢,跟上题不能说十分类似吧,只能说一模一样,只是s变大了而已,但实践证明,它并没有影响我们格攻击成功。(所以说不理解出题人的预期效果是什么,希望能讲一讲)
那么攻击思路就同上
解答:
1 | |
总结
打ctf以来最有感觉的一场比赛,酣畅淋漓,也是燃尽了,感谢队友的带飞。
总结自己的做题量还是太少,对于很多原本应该一眼看出来的问题还是犹犹豫豫的,甚至不敢相信自己思路是对的,后来被hint拉回原本的思路才坚持做出正确结果。
因此日后还要加倍努力,争取不拖队友后腿!