CISCN 往年题练习
2018
oldstreamgame
先总结一下关键计算关系:
$i=R&mask$
$out=i中1的个数\mod2$
$output = R[:-1]+out$
每8位$out$组成一个 key 的字符
然后我们可以发现一个关键点:
key 中每一位的生成都和前边 32 位相关,即跟生产时的 R 相关。
也就是说
$R_0 = f_{32}…f_1$
$R_1=f_{31}…f_1out_1$
$…$
$R_{31}=f_1out_1…out_{31}$
然后我们现在知道 800 位的 out,所以肯定知道 $out_{32}$,然后我们就可以尝试$f_1$的值是 0 还是 1,看$f_1$是哪个值得时候会生成$out_32$,以此类推就能得到 flag 所有 bit 值。
exp:
1 | |
sm
$gen512num:$
- $order$为 512 个 512 bits 的随机数组成的数组
- $p_i$ 为 $512-order_i+10$ bits 的素数
- $pre_i$ 为 $p_i$ 的前 $512-order_i$ 位拼接上 1
- $ps_i$ 为 $pre_i$ 补齐到 512 位
ps 共 512 组
choose 是 512 bits 素数,bchoose 是其二进制形式
若 $bchoose_i == 1$,r 就异或上 $ps_i$
ef 是 AES 加密后并使用 base64 编码后的结果
思路分析:
现在的目的就是求 key,也就是求 choose。
现在就是要用 r 尝试异或 $ps_i$,更关键的是,我们知道每个$ps_i$都是以$10…$结尾的,而且0的个数还不一样,这样我们就能从 r 的结尾结构来求 flag 了。
exp:
1 | |
crackme
加密:
- r 是 32 bits 随机整数
- $ret_0=2^r\mod p$
- $ret_1=h^r\mod p \times bVal$
解密:
- $s = (ret_0^x)^{-1}\mod p$
- $plain=ret_1*s \mod p$
我们这里肯定是求不出私钥 x 的,因为我们没有任何和私钥 x 相关的信息可以拿到。
但是如果对数据大小足够敏锐的话,可以发现 r 仅仅是 32 bit 的随机整数,我们知道,正常大小在 $2^{32}$ 以内,我们就可以尝试爆破了,而且这里我们还可以使用 BSGS 算法来进一步降低算法的复杂度。
我们利用这个 $ret_0=2^r\mod p$ 求出 r,之后就可以求出 $ret_1=h^r\mod p \times bVal$ 中的明文 bVal。
exp:
1 | |
2021
RSA
flag 被分成了三份,每份都分别进行了 RSA 加密,所以显然是一个对 RSA 多种题型的一个缝合,看着都比较简单。
第一段 e = 3,明显是低加密指数攻击,首先尝试直接开方或者小范围爆破。
第二段对同一段密文在相同的模数下进行了加密,因此是共模攻击。
第三段明显是 p 的高位泄露攻击。
接下来我们逐个进行求解即可,最后完成拼接。
exp:
1 | |
small
$x,y$的都是$(2^{70},2^{71})$的数,看着不是很大,都是小根,要求解方程
$c=(1+axy^2+bx^2y)\mod p$
尝试 coppersmith 求小根
exp:
1 | |
classic
考察古典密码
1 | |
直接上工具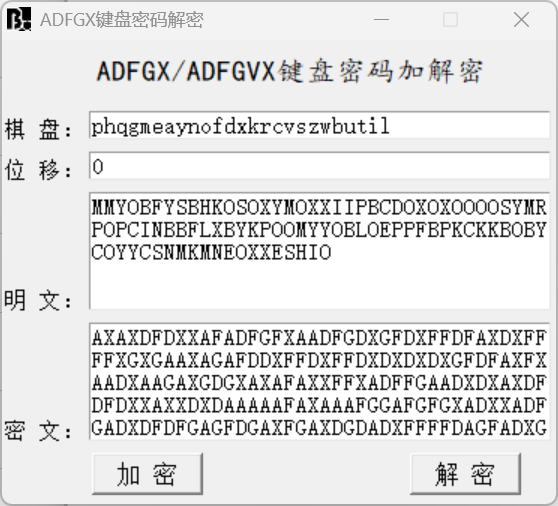
得到
1 | |
然后尝试栅栏密码解密找到开头和 ciscn 结构一致的明文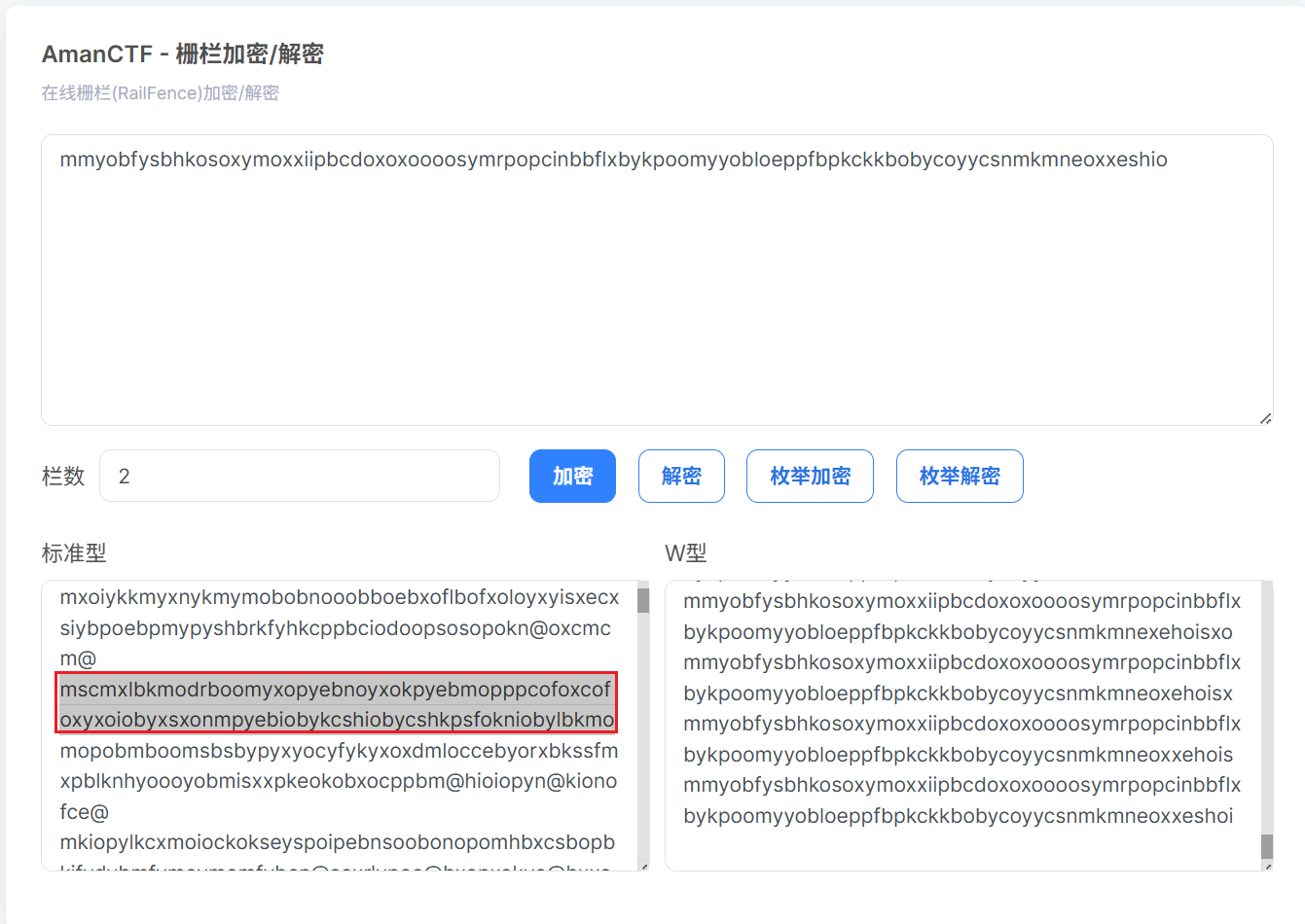
尝试 casar 密码爆破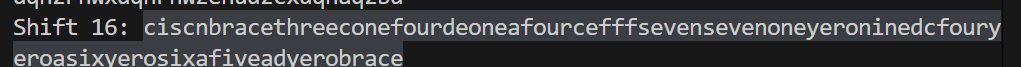
成功找到 ciscn 开头的明文
1 | |
然后把字符串中的数字英文换成数字,brace 是大括号的意思,但是其中yero是 0。
1 | |
move
p,q 都是 3k+2 形式的素数,且 p < q
$gen:$
- n = pq
- bound = $\sqrt{2pq}//12$
- x 为 $(1,\sqrt{\sqrt{2pq}//12})$ 中的随机整数,y 为 $(1,\sqrt{2pq}//12)$ 中的随机整数
- $zbound = ((p-q)n^{0.25}y)//(3(p+q))$
- $z = zbound - ((p+1)(q+1)y+zbound)\mod x$
- $e=\frac{(p+1)(q+1)y+z}{x}$,可以推出$\frac{e}{n}=\frac{y}{x}$
然后 add 和 mul 一看就像是 ECC,我们要敏感,比如看见 $p\equiv 2 \mod 3$,就要知道,对应的曲线通常是 $y^2=x^3+1$,曲线的阶是 $(p+1)(q+1)$。
我们从 output 中可以看到,e 是非常大的,我们还能看到敏感信息 $n^{0.25}$,很容易联想到 Wiener 攻击。
至于 h1 和 h2,貌似出题人想要缝上 coppersmith,但实际上根本用不到。
exp:
1 | |
2024
rasnd
flag 被拆成两段加密
$crypto1:$
- $hint1 = x_1p+y_1q-0x114$
- $hint2=x_2p+y_2q-0x514$
- 其中$x_1,x_2\in (0,2^{11})$,$y_1\in (0,2^{114})$,$y_2\in(0,2^{514})$
这时候我们又需要敏感了,大小在 $2^{30}$ 以内的数,我们其实都可以考虑爆破的,现在 $x_1,x_2$ 甚至只有 $2^{11}$ 以内,即使相乘也只有 $2^{22}$,可以直接爆破 $x_1,x_2$。
$crypto2:$
- $hint \equiv (514p-114q)^{n-p-q} \equiv (514p-114q)^{phi-1} \equiv (514p-114q)^{-1}\mod n$
很明显,我们能求出 $(514p-114q)$ 整体的值,解方程组即可
exp:
1 | |
fffffhash
分析一下思路
目的是输入一串十六进制字符串,让它的十进制转换为字节,经过giaogiao函数运算之后得到的值等于题目给出的预期值 giao
我们重点看一下函数giaogiao:
- 基值 $base_num$,参数 $x$,模数 $2^{128}$
- 遍历每个字节,每次 $base_num=(base_num\times x)\mod 2^{128}$。然后跟字节异或 $base_num = base_num \oplus i$
每次的 $i$ 都是一个小值,可以把异或 $i$ 当作加减一个小值 $a<255$,拿前四轮举例一下:
$G \equiv (((base\cdot x+a_1)x+a_2)x+a_3)x+a_4 \equiv base\cdot x^4+a_1x^3+a_2x^2+a_3x+a_4 \mod M$
造格:
$$
(a_1,a_2,a_3,a_4,-1,k)
\begin{pmatrix}
1 & & & & & & x^3 \
& 1 & & & & & x^2\
& & 1 & & & & x\
& & & 1 & & & 1\
& & & & 1 & & G-base\cdot x^4 \
& & & & & 1 & p &
\end{pmatrix}
=(a_1,a_2,a_3,a_4,-1,k,0)
$$
具体代码待补充,,,